Introduction
The OIDC auth method allows a user's browser to be redirected to a configured identity provider (Azure AD), complete login, and then be routed back to Vault's UI with a newly-created Vault token.
Prerequisites (if applicable)
-
Azure Active Directory
-
Vault
Use Case
This article show how to enable OIDC auth method in a child namespace on a Vault server
Azure Active Directory settings:
-
Log in to Microsoft Azure.
-
Go to Azure Active Directory.
-
Save the Tenant ID because this will be used later in the OIDC discovery url on tenantID section
-
Go to App registration and add new registration.
-
Save Application (client) ID because it will be used later to set oidc_client_id.
-
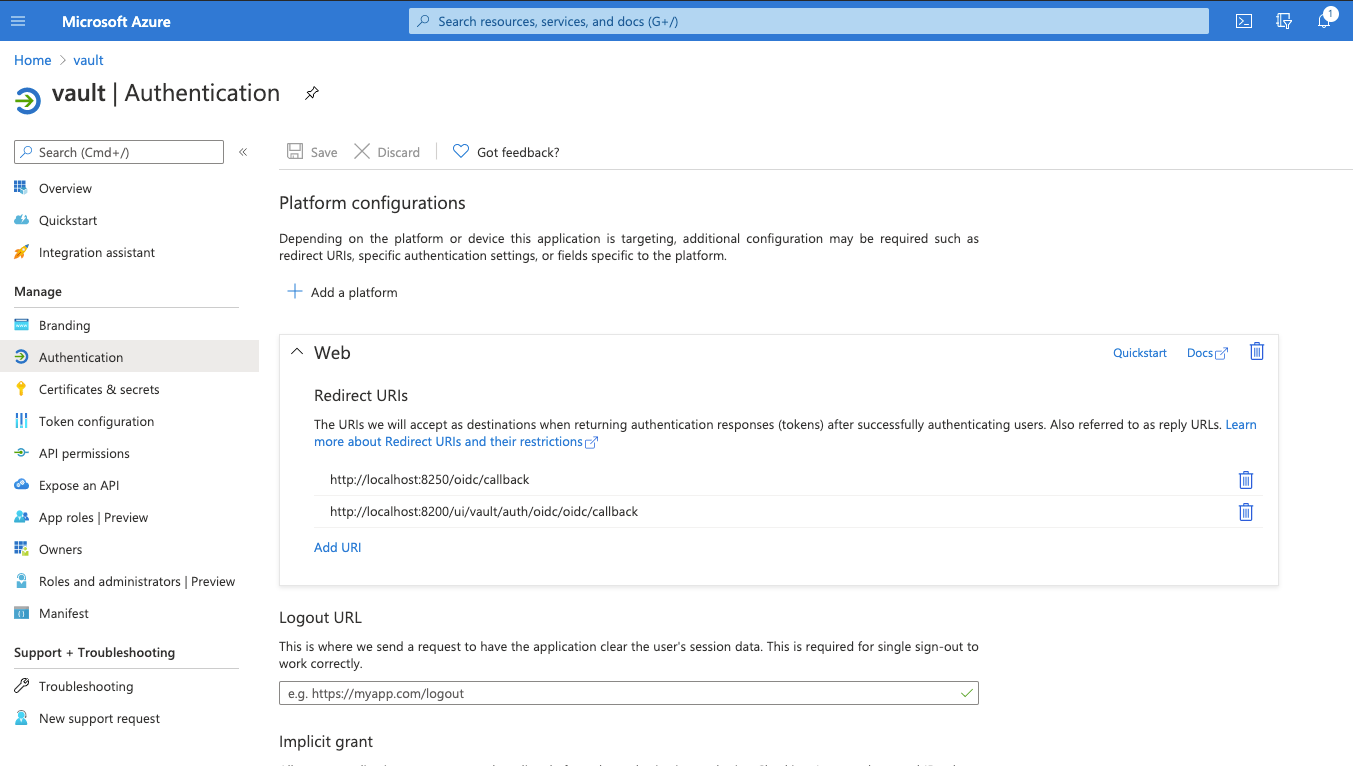
Go to Authentication and add a platform, select Web and enter the URIs (including the namespace in the callback). This can usually be:
http://localhost:8250/oidc/callback. -
Go to Certificates & secrets and click New client secret. Save the Secret Value (not Secret ID) as it will be later set as oidc_client_secret.
-
Go to API permissions and add a permission for Microsoft Graph Application permission and select GroupMember.Read.All.
Instructions for Vault
If you don't have already a vault server that is running, start Vault dev server with the following command:
*** Never run Vault in dev mode in production environment ***
$ vault server -dev -dev-root-token-id="root"
Open another terminal and export the environment variable VAULT_ADDR for the vault CLI to address the Vault server:
$ export VAULT_ADDR='http://127.0.0.1:8200'
Login with a token with an admin policy or with root token if the vault dev server is used:
$ vault login root
If the vault server doesn't contain any namespaces, create a new namespace called education that has a child namespace training:
$ vault namespace create education
$ vault namespace create -namespace=education training
Example of how to enable OIDC authentication method in the child namespace training:
$ vault auth enable -namespace=education/training oidc
Configure the OIDC auth method:
$ vault write -namespace=education/training auth/oidc/config \
oidc_discovery_url="https://login.microsoftonline.com/tenantID/v2.0" \
oidc_client_id="your_client_id" \
oidc_client_secret="your_secret_id" \
default_role="reader"
Configure OIDC role for Vault versions before 1.6.0:
$ vault write -namespace=education/training auth/oidc/role/reader \
bound_audiences="your_client_id" \
allowed_redirect_uris="http://localhost:8250/oidc/callback?namespace=education%2Ftraining" \
allowed_redirect_uris="http://localhost:8200/ui/vault/auth/oidc/oidc/callback?namespace=education%2Ftraining" \
user_claim="sub" \
policies="default"
For Vault versions 1.6+ OIDC role will be configured without the namespace as a query parameter in the redirect URI:
$ vault write -namespace=education/training auth/oidc/role/reader \
bound_audiences="your_client_id" \
allowed_redirect_uris="http://localhost:8250/oidc/callback" \
allowed_redirect_uris="http://localhost:8200/ui/vault/auth/oidc/oidc/callback" \
user_claim="sub" \
policies="default"
Results
Test to login via CLI:
$ vault login -namespace=education/training -method=oidc role="reader"
If authentication is successful, the following details should be seen:
Complete the login via your OIDC provider. Launching browser to:
https://login.microsoftonline.com/tenantID/oauth2/v2.0/authorize?client_id=clientIDe&nonce=nonce&redirect_uri=http%3A%2F%2Flocalhost%3A8250%2Foidc%2Fcallback&response_type=code&scope=openid&state=state
Success! You are now authenticated. The token information displayed below
is already stored in the token helper. You do NOT need to run "vault login"
again. Future Vault requests will automatically use this token.
Key Value
--- -----
token s.2DgqQBpeve3jf3x6BaNXRWWd
token_accessor o3P6HeKrh4CsaTSD9dJvEIUy
token_duration 768h
token_renewable true
token_policies ["default"]
identity_policies []
policies ["default"]
token_meta_role reader
