Background and goal:
Vault 1 and Vault 2 are two separate stand-alone Vault clusters where one protects another's master key. Vault 2 is the vault cluster with the transit secret engine, it is the encryption service provider, and its transit key protects the Vault 1 server's master key. Vault 2 is the vault cluster auto-unsealed by Vault 1. This KB is going to cover the process of migrating Vault 2 from Transit Auto-unseal back to Shamir seal type.
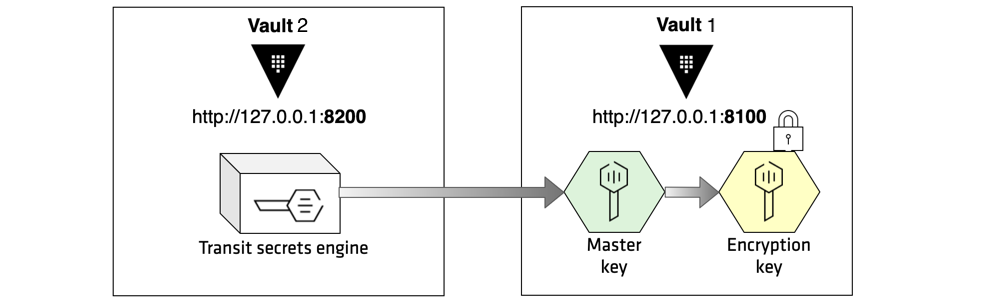
Note: Following steps are designed for a Vault cluster with a single node (active). In the case for a Vault cluster with multiple nodes, perform following steps for all the standby nodes first, one at a time. It is necessary to bring back the downed standby node before moving on to the other standby nodes, specifically when Integrated Storage is in use for it helps to retain the quorum. Then Step down the final active node. One of the seal migrated standby nodes will become the new active node.
Steps:
1. Stop Vault1
2. Update Vault1 server configuration file seal "transit" by adding disabled = "true" into seal stanza
# Example seal stanza for vault1
seal "transit" {
address = "http://127.0.0.1:8200"
disable_renewal = "false"
key_name = "autounseal"
mount_path = "transit/"
tls_skip_verify = "true"
disabled = "true"
}
3. Save the change and restart Vault1 server with the command:
$ vault server -config=config-autounseal.hcl
Run vault status, you will find that seal type is now Shamir, previously was Recovery Seal Type, and vault is sealed
❯ vault status
Key Value
--- -----
Seal Type shamir
Initialized true
Sealed true
Total Shares 5
Threshold 3
Unseal Progress 0/3
Unseal Nonce n/a
Seal Migration in Progress true
Version 1.8.4+ent
Storage Type file
HA Enabled false
4. Initiate an unseal command with the flag `-migrate` and enter the first recovery key:
$ vault operator unseal -migrate
5. Type in the rest of the remaining keys with vault operator unseal -migrate
6. Verify result with command vault status, seal type value is shamir, and vault is unsealed
$ vault status
Key Value
--- -----
Seal Type shamir
Initialized true
Sealed false
Total Shares 5
Threshold 3
Unseal Progress 0/3
Unseal Nonce n/a
Version 1.8.4+ent
Storage Type file
HA Enabled false
7. Stop Vault 1 and open its server configuration file again, delete the existing seal "transit" stanza.
Result:
Transit seal to Shamir seal migration is now finished, vault operator now can unseal the vault with Shamir unseal keys.
If further seal migration is needed, vault operator can continue the migration process to either a new Vault cluster with transit secret engine, or other trusted cloud providers (AliCloud KMS, Amazon KMS, Azure Key Vault, and Google Cloud KMS).
There is another KB article about Vault Seal Migration, migration between Shamire and other cloud seal types.
Reference:
1. Auto-unseal using Transit Secrets Engine
3. transit seal