All traffic sent through the Consul Connect Service Mesh is encrypted. If you need or want to verify that traffic is being encrypted, you can follow this process.
Prerequisites
To perform this test, you'll need the following:
- An environment with two services deployed. They should be scaled such that there's only one instance of each service.
- The ability to start/stop said services.
- Access to either SSH into the VMs running the Consul sidecars or the ability to exec into containers if you're running in a Kubernetes environment.
Verification Process
- Ensure both services you're testing with are stopped.
- Bring up one of two services that communicate over the service mesh.
- Connect to that service's consul client sidecar container (either via SSH or by using
kubectl exec). - Install tcpdump (either via your distribution's package manager or if you're using a container by running
apk add tcpdump). - Start a packet capture to a location you can access from your local machine:
tcpdump -i eth0 -w traffic.pcap. Make sure you're capturing on the interface the sidecar is communicating over. - Bring up the second service and confirm it's communicating with the first service (i.e., perform actions that exercise communication between services to make sure it's working).
- Stop the tcpdump and examine the pcap file in wireshark. If you like, you can filter the capture using
tls.record.content_type == 22to only see the TLS handshake packets. You should see something like this: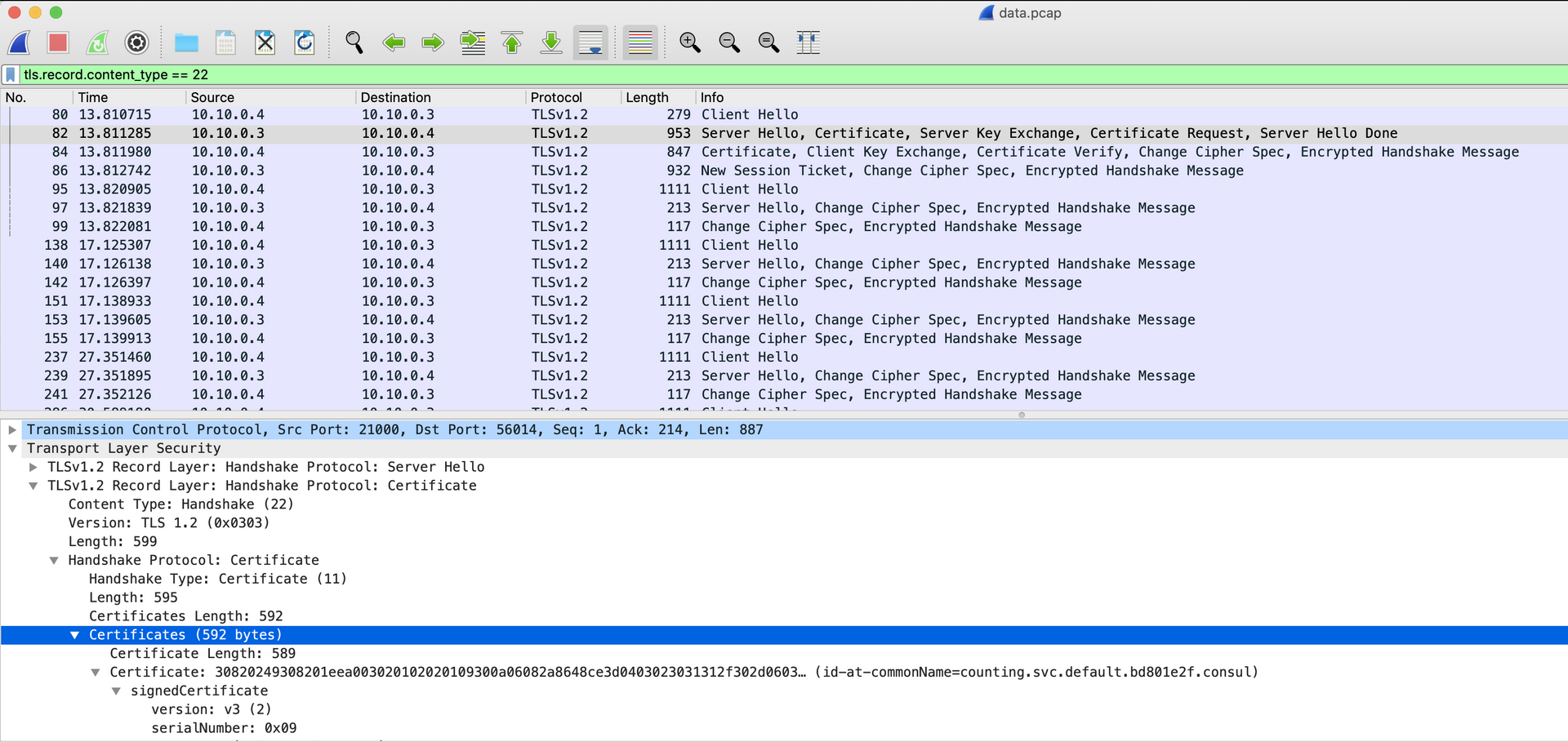
The Certificate, Server Key Exchange, Certificate Request, and Client equivalents indicate that an mTLS session is being started. Note that you'll only see the lines referencing those if you have the packet capture already running when the two services first communicate. Those actions only happen on their first interaction and subsequent requests will not contain the initial handshake that contains the certificates.
While examining the traffic, you'll be able to tell traffic is encrypted because you won't see any of the raw HTTP requests the services are making to each other in the packet capture. If the communication was happening in an unencrypted fashion, you would see all of those requests in plain text.